
We Provide Cybersecurity Consulting Services to Small and Mid-Sized Businesses and NonProfits
Your IT team juggles lots of demands, high expectations, and high pressure. They work hard to make sure your organization hums along performing at its best with the network, systems, and tools you need to deliver great service to your clients and key stakeholders.
We’re here to help.
Bad actors are on the job 24/7/365 to gain access to what you’ve worked so hard to build. They care about nothing but making easy money with your data and exploiting any vulnerability they can find.
That’s where we come in.
As cyber security consultants, we provide the tools needed to protect your data and cyber assets. It’s our mission to support your IT team so they can stay focused on their mission.
We don’t replace your existing IT department. We partner with them to help you achieve your business goals. And that includes managing the risks of a cyber incident.
The benefits of working with us include…
An impartial assessment of your risks
A prioritized plan to reduce those risks
Proven tools to address your risks
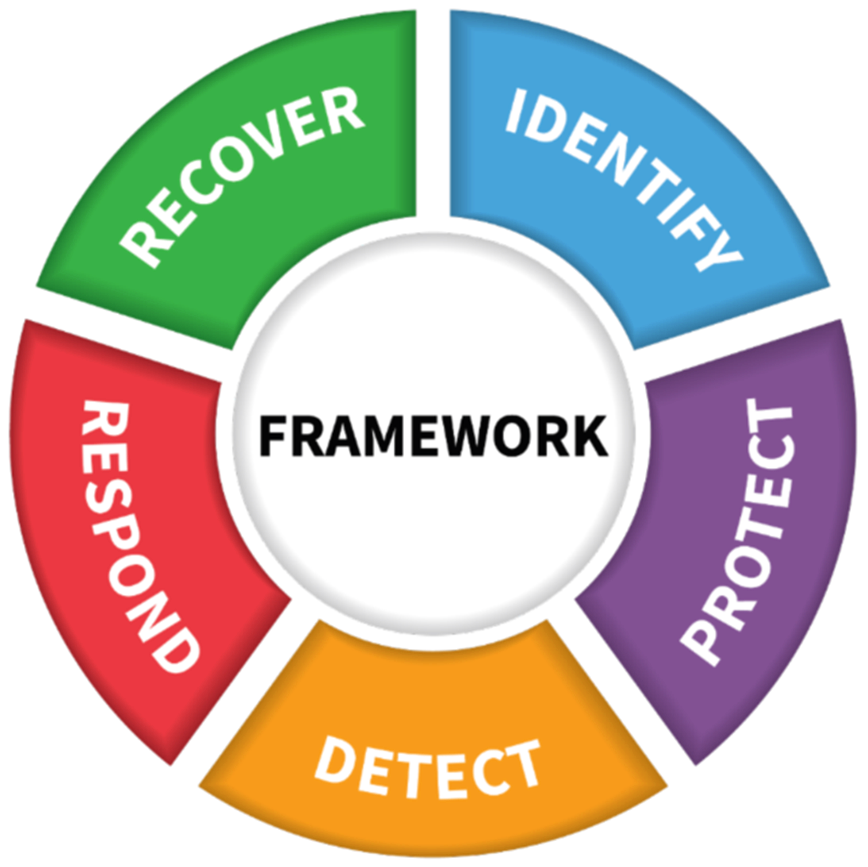
We Follow Industry Protocols to Create
a Cybersecurity Strategy Based on Your Needs and Goals
It’s more than just cyber security. It’s about cyber resilience – being adaptable and strong.
The US National Institute of Standards and Technology (NIST) framework is a powerful, standard protocol organizations use to acknowledge, plan for, and manage cyber risk exposure.The framework provides structure to solve an immediate cybersecurity problem and manage ongoing risks.
Bad actors are on the job 24/7/365. They continuously adapt in order to break into your network.
Constant vigilance is required to stay one step ahead or to recover quickly if they do gain entry.
Cybersecurity Isn’t a One Time Task.
Because bad actors work in the background - and cybersecurity isn’t something truly tangible like a lock on the door - it’s easy for employees to become complacent and for leadership to lose focus on it.
That’s why working with an outside cyber security consulting firm provides a strong ROI.
We're impartial and focused on staying one step ahead of the hackers, fraudsters, and other bad actors out there so you stay focused on what you do best.


Take Steps to Build and Maintain Your Cybersecurity Plans to Make Your Organization Cyber Resilient
The steps we take clients through are part of a standardized, proven process. The solution is always customized to your organization’s needs, goals, and size.
Our Trusted Partners













We Serve Businesses and NonProfits with Multiple Locations and Hybrid Staff
The new reality of hybrid work - a combination of working from home, in the field, and in the office - provides a new set of challenges.
We understand those challenges and are experienced at meeting them.
It’s Easy to Get Started
Have a no-obligation Next Best Move call
We’ll discuss your cyber security needs, concerns, and goals. We'll let you know what we think your next best move is.
Just click the button to schedule a conversation and we’ll get back to you by the end of the next business day.
Not Ready to Talk Yet?
Let’s Keep in Touch.
We’re building a learning center to give folks like you the information needed to get their heads around the ever evolving, big topics of cybersecurity and telecommunications.
Let’s keep in touch so you get notified of new content when we create it.
